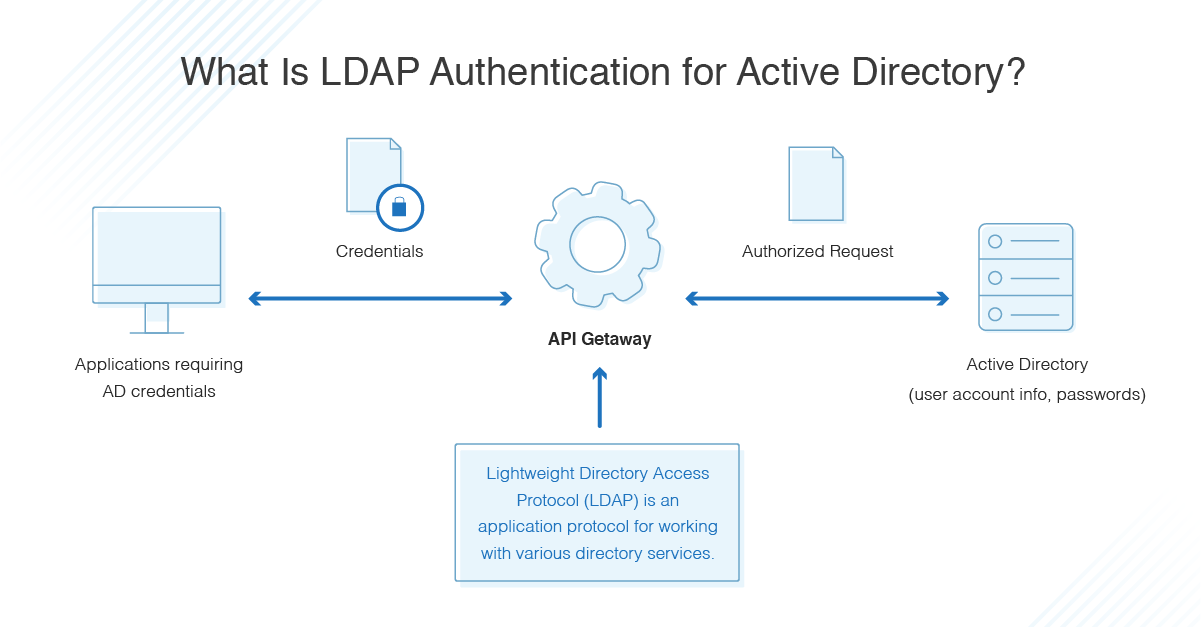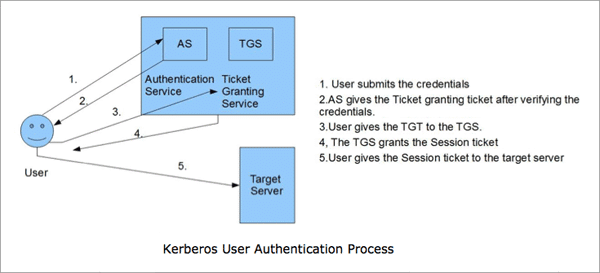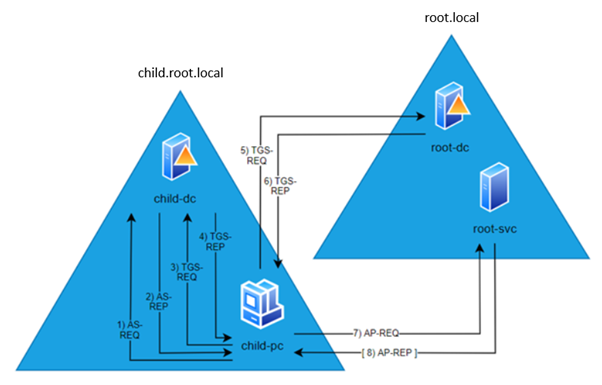
SID filter as security boundary between domains? (Part 1) - Kerberos authentication explained — Improsec | improving security

Deploy a Read-Only Domain Controller (RODC) on Windows Server 2016 | ITPro Today: IT News, How-Tos, Trends, Case Studies, Career Tips, More